Spooky Security Trends
With Halloween just around the corner, we take a closer look at scareware.
As the Internet evolves, so does the sophistication of cyber criminals and their methods. Even the savviest of computer users can fall victim to online threats.
You may not be familiar with the term scareware, also known as rogue security software, but there's a very good chance that you or someone you know either has experienced it, or will in the near future. As malware writers inundate the web with fake anti-malware programs, this kind of trickery is becoming more and more common, and now poses one of today's greatest security challenges to computer users. Scareware has become a very lucrative industry for cyber criminals, and it does not seem to be slowing down.
What is Scareware?
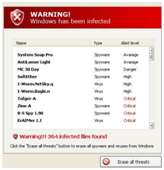
Scareware, or rogue security programs, normally start as a popup that claims the web user's PC is infected with malware. It then prompts the user to purchase the fake security software - which is actually malware in disguise — in order to remove the "threat". Essentially, it is malware pretending to be genuine Internet security programs, with the aim to steal your money, private information, or to expose you to other high risk cyber threats.
How does it End Up on Your Computer?
Scareware is distributed in a variety of ways, using social engineering tactics to deceive and mislead people. It can be encountered almost everywhere on the web today. For example:
Search Results:
Be careful what you click. Look at the link before you click it. Scammers prey on unsuspecting computer users by exploiting misspelled URL's and use popular search queries about celebrity news and other hot topics to lure users to their website. Clicking on such a link could launch the scareware.
Fake Ads:
Ads that look like they come from a legitimate company can in actuality be malware. These ads have even appeared on high-profile sites, such as FoxNews, New York Times, and MSNBC. If clicked on, either a fake malware scan is triggered, or a warning is shown in an attempt to trick the user into believing their computer is already infected with malware, and that purchasing the application will help them get rid of it.
Social Networks:
This past year, we have seen an explosive rise in click-jacking attacks and other similar scams on social networks. Tainted links can easily be distributed this way. Again, be careful what you click.
Spotting the Fakes
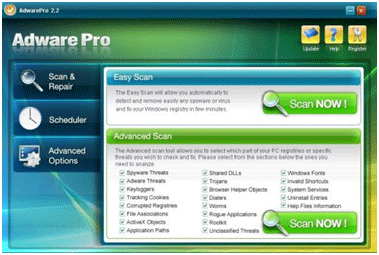
It is nearly impossible for most people to spot a rogue security program by merely looking at it. Most of them have a professional-looking website that appears to be from a legitimate company

The user interface often looks very similar to trusted security products.
How Can You Avoid Scareware?
What can you do to help prevent the spread of scareware and make sure that you don't fall for the cyber criminals' tricks? Follow these tips below to tell what's real and what's not when it comes to security software — and share them with friends and family who may be vulnerable to scareware.
- Do not fall for scare tactics. While browsing sites, be cautious of pop-ups warning you that your system is infected and offering a product to clean it up. Never pay for a program that installed itself to your computer. This is a hallmark of rogue software.
- Use security software with real-time protection and keep it up-to-date. If you know that you have anti-virus, anti-spyware, and a firewall on your PC, you can safely ignore security alerts you receive that do not come from your chosen security software provider. (Rogue security software will often try to lure computer uses by using legitimate looking pop-up messages that appear to be security alerts.) Also, most anti-malware programs, like Ad-Aware, will help keep you protected from rogues because they can detect and remove these programs.
- Access experts at the Lavasoft Support Forums or other security forums and ask about the software you are considering before you decide to purchase it.
- Read the software reviews at reputable sites like Download.com. Do not blindly trust individual sites offering security products. You can also refer to Lavasoft's Rogue Gallery to check to see if a program in question is listed as a rogue.
- Ask knowledgeable friends and family members about quality software they use. Keep in mind that when you search for trustworthy security software online, rogue products can, and often do, appear in the search results list.
- Practice online skepticism. Be aware that rogue security software does exist on the Web, and be vigilant about avoiding it. These programs are designed to appear genuine - meaning they may mimic legitimate programs, use false awards and reviews to rope you in, or employ other deceptive tactics. It's also a good idea to familiarize yourself with common phishing scams, and to be cautious of links in e-mail messages and on social networking sites.
|